For starters, An MSI Afterburner is a GPU feature that lets users configure overclocking, record video, make fan profiles, and monitor their installed graphic card and CPU utilization. Well, this feature can be used by users with almost every graphic, which makes it usable for millions of users around the world who then modify its settings as per their requirements, i.e., To attain lower temperature, improve game performance, and more. Well, all these things make this tool a good target for attackers who look to target Windows power users or Gamers who uses powerful GPUs, which they can take over to it use for cryptocurrency mining. According to Cyble, in the past three months, more than 50 websites have appeared on the internet which are mimicking the Official MSI Afterburn website and pushing XMR miners alongside the information-stealing malware. Read: AXLocker Group of Ransomware Steals the Discord Accounts of Infected Users To add to this, the campaign used identical domain names to deceive users into believing that they are the legitimate MSI Afterburn website which is easier to promote using Black SEO. These are some of the domains identified by Cyble.
msi-afterburner–download.site msi-afterburner-download.site msi-afterburner-download.tech. msi-afterburner-download.online msi-afterburner-download.store msi-afterburner-download.ru msi-afterburner.download mslafterburners.com msi-afterburnerr.com
Furthermore, in other cases, the domains did not use the MSI brand and were possibly promoted through messages, social media posts, and forums.
git.git.skblxin.matrizauto.net git.git.git.skblxin.matrizauto.net git.git.git.git.skblxin.matrizauto.net git.git.git.git.git.skblxin.matrizauto.net
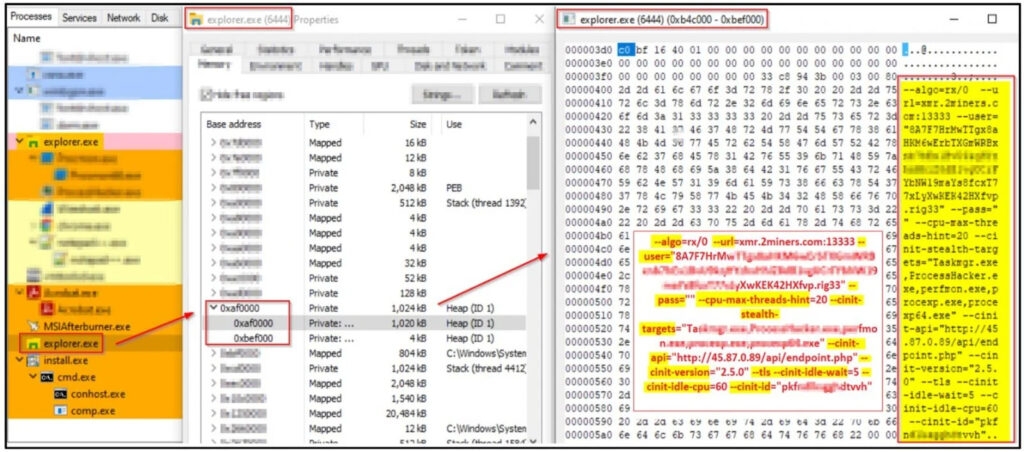
When the fake MSI Afterburner setup file is executed (MSIAfterburnerSetup.msi), the valid file will be installed. However, the installer will silently drop and run the RedLine information-stealing malware and also the XMR miner in the infected device. The XMR miner is then installed through a 64-bit Python executable named “browser_assistant .exe’ in the Local Programme Files directory, which inserts a shell in the process created by the installer. The Shell code fetches the XMR miner from the GitHub archive and then directly injects it into the memory of the explorer.exe process, and as the XMR miners never interact with the disk, so chances of it getting detected by the security products are pretty slim. After that, the XMR miner links the miner pool by using a hardcoded username and password and then gives the basic system information to the threat attacker. Read: Phishing Email Kit Targeting North Americans During Holiday Season! Well, one of the functions that the miner uses is the “CPU maxed thread” set to 20, which exceeds the most CPU threads so it is set to consume all the available power. The XMR miner is put to mine only after an hour, and since the CPU goes into idling, this indicates that the compromised PC is not being used for any resource-hungry task and is possibly left unattended. Moreover, it uses the cinit-stealth-targets function, which is essentially an option to pause mining and clear the GPU memory when a particular program listed under the “stealth targets” are launched. These could very well be the programs that help the victim to identify malicious processes, i.e., antivirus, hardware resource viewer, and more. In this scenario, the miner which tries to hide from the windows applications are taskmanager.exe, procexp.exe, Processhacker.exe, perforn.exe, and procexp64.exe. At the same time, the XMR miner is silently taking control of your resources (Monero); the RedLine had already run in the background stealing browser data, cookies, passwords, and any possible cryptocurrency wallet that there is. Sadly, almost all the Fake MSI Arterburn campaign components have bad anti-virus software detection, so much so that a report by VirusTotal mentions that the MSIAfterburnerSetup.msi setup file is only detected by 3 security software out of 56 & while the browser_assistant.exe is only detected by 2 out of 67. Read: Mirai RapperBot Malware Attacking Online Game Servers with DDoS